Proving that money and target size aren’t the primary concern for all hackers, a cyber attack by hacktivists on water equipment in the western Ireland area of Erris, County Mayo, left 160 households without a supply for two days [The Record. 12 December 2023].
Hacktivists value impact and headlines over money to promote a political agenda or social change.
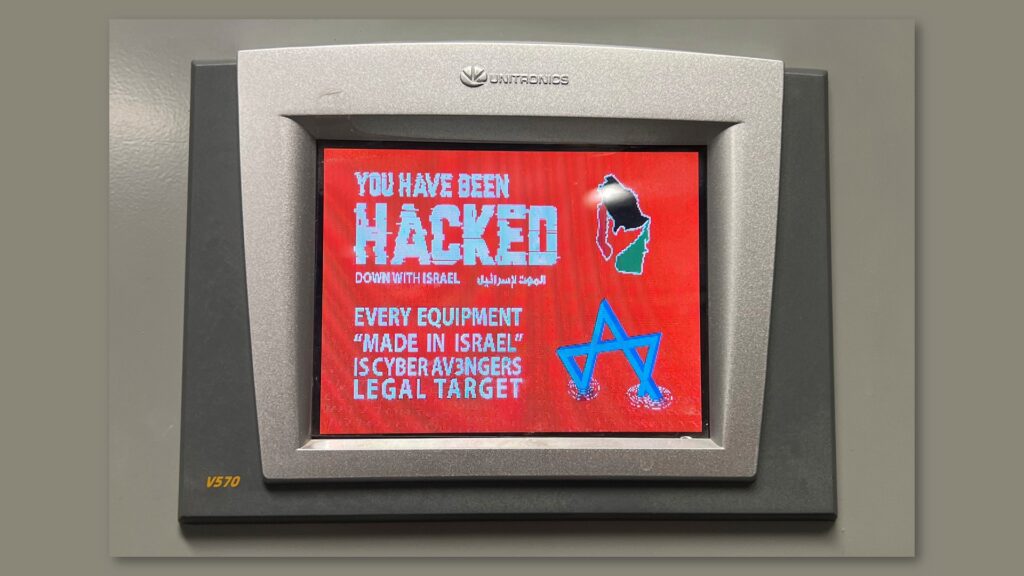
The compromised equipment, the Unitronics programmable logic controller (PLC), was made in Israel. The hackers confirmed they were attacking water and energy facilities using products from Israel.
Other water utilities around the world were also hit.
PLCs are used in water and wastewater systems to control and monitor various stages and processes, including turning on and off pumps at a pump station to fill tanks and reservoirs, flow pacing chemicals to meet regulations, gather compliance data for monthly regulation reports, and announce critical alarms to operations.
The Unitronics PLC was—and for those who haven’t taken remedial action, still is—vulnerable to attack due to its simple, default password of ‘1111’, and having the ability to be connected directly to the open internet.
Such simple default settings have been common to operational technology (OT) in a range of settings, not just PLCs in water systems. The settings are often documented in user manuals that can be found online.
Whilst manufacturers are increasingly putting safeguards in place to reduce these sorts of vulnerabilities, equipment already in the field may remain susceptible.
OT can have a lifecycle of many, many years.
How can organisations defend against simple OT cyber attacks?
With the Unitronics incident in mind, here are three fundamental steps organisations can take in an effort to defend against a similar attack.
- Understand what operational technology you have. Build a register that includes manufacturer, equipment type, software and firmware version numbers, and what role the equipment plays in service delivery. This will help proactively manage what you have, potentially identify risks to be managed, and respond in a coordinated manner if things go bad.
- Review settings, including passwords and other access controls, to minimise or eliminate the risks of hackers breaking through using default settings.
- Monitor for security updates. This can often be via the manufacturer’s website. Respond promptly to advisories, because hackers will also be monitoring in an effort to get ahead of compromised organisations.
💡 “It is the little things that are vital. Little things make big things happen.”
John Wooden
Never a truer saying, whether it’s little operators being taken offline by hacktivists to make the big headlines, or basic cyber security practices preventing huge disruptions.
Monthly cyber security insights, news and tips direct to your inbox
More information here. You can unsubscribe at any time. See Privacy Policy for further details.
